The challenge
This challenge was one of the 25 (minus a few canceled ones) written and organized by TrendMicro for their TMCTF 2015. I played with the Swiss team “On est pas contents” and I won’t disclose how badly we ranked 🙂 Some challenges were really boring (a crossword where half the solutions come from the commercial product aisle? Not for me). Some were frustrating, and one was really great: Poison Ivy network capture.
TrendMicro was very fast in shutting down the whole CTF website, so I can’t get an hand on the original challenge text. From memory:
A hacker was caught using Poison Ivy on a real system. Please understand what he was doing to get the flag. (ps: password is admin).
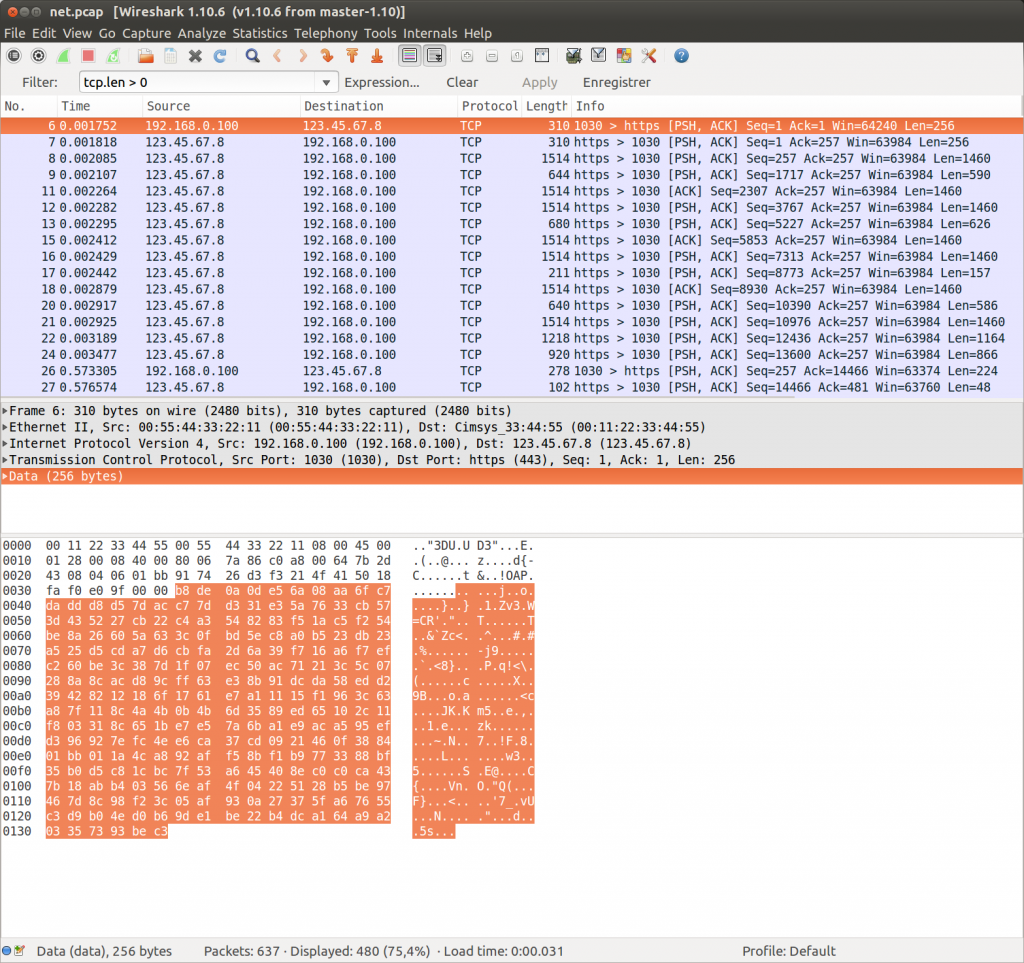
With that exciting information I start downloading the pcap. Opening in wireshark, it appears it’s a single TCP connection on the 443 port. This doesn’t look like https and the wireshark dissector doesn’t want to parse it. Right click on a packet, “Decode as…” and check “do not decode” makes us see the raw exchange.
Continue reading “TrendMicro CTF 2015 : Poison Ivy (Defense 300) write-up”